The availability of the writings of various authors has increased instances of plagiarized text. To estimate the authenticity of the work the writing is cross-verified across previous writings. Plagiarism check is a process which scans the complete writing.
Plagiarism
Plagiarism is a factor which creates the line between the genuine work & copied work of an individual. It is something to be understood instead of ignoring it. Students need to understand how different plagiarism software work in order to create perfectly plagiarism free assignments.The Internet is linking many repositories to its users.The software explores different repositories to find the similar writing. Different approaches can be adopted to find the legitimacy of the writing. The breaching of the copyright policy is minimized using this approach.
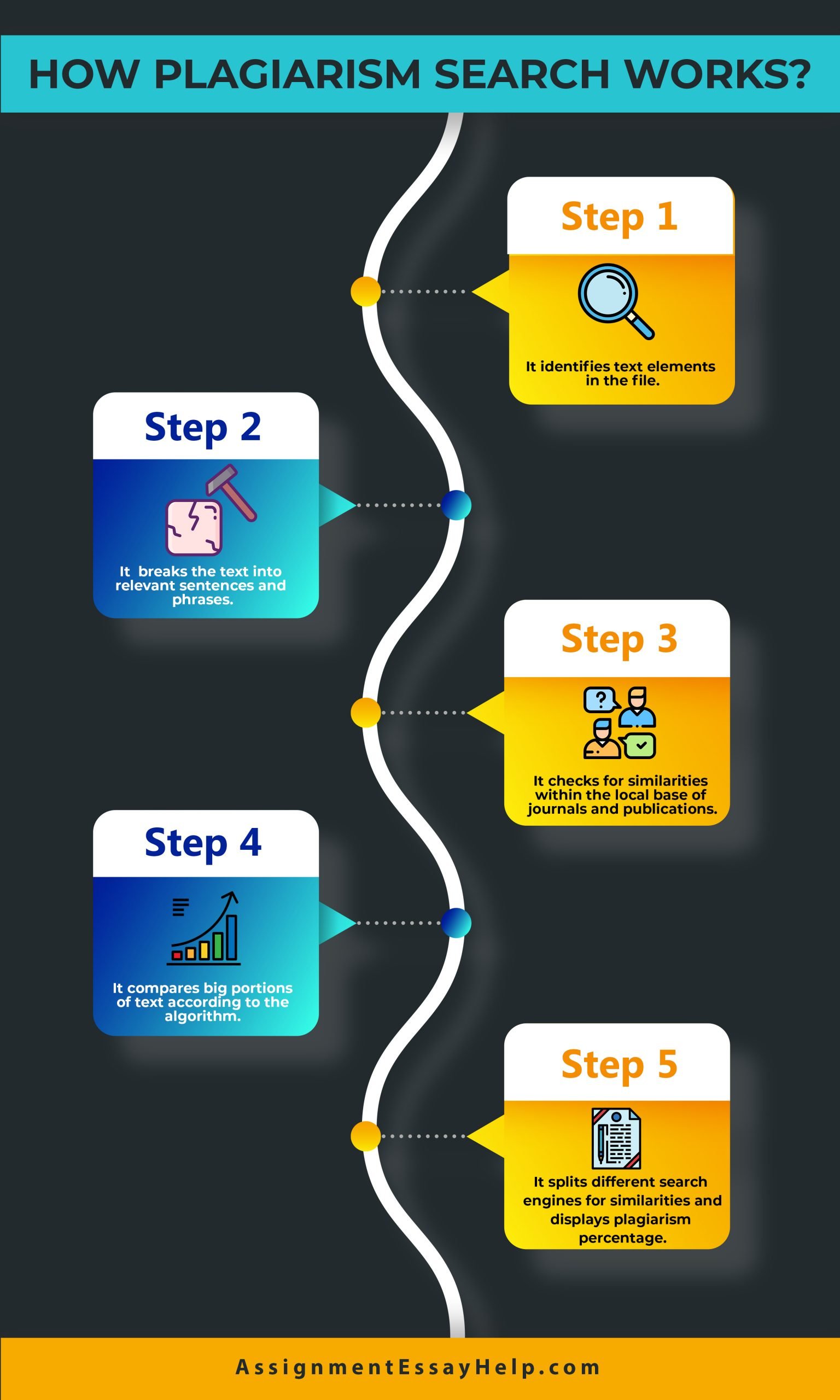
The document to be authenticated is used to spot the similarity in writing. This process is known as Plagiarism detection. The procedure is adopted to scan writings in scientific, art design and source code. The process can be manual or software-assisted.
Rogeting is a procedure used to avoid the detection of plagiarized text. The enough word substitution is done to get a positive outcome. The information retrieval systems use the repository to process, plagiarism detection system.
There are two generic detection approaches adopted to locate the plagiarized text. The genuine set of documents is kept as a reference. The suspicious document is compared with the reference to locate the plagiarized text. A document model is used to make comparison between the source document and reference.
Another approach is known as intrinsic plagiarism detection system. The approach does not use any external source to analyze the source. The unique writing style of the authors is considered in this approach. This procedure is not capable of detecting the plagiarized text without human intervention.
Different approaches are used to detect the plagiarized text in the source document. Information science assignment help narrates different approaches.
Fingerprinting
This is is an approach used by a large population. A set of multiple sub strings is selected. This set represents the fingerprints. The elements of the same are known as minutiae. The fingerprint is computed in the source document. The querying minutiae are mapped to pre-computed index of the fingerprints. The threshold value is set to provide results of the procedure. A subset of minutiae is used to speed up the process. The computational resources and time are the limitations of this approach.
String matching approach
A prevalent approach used in the information science field is used to form second approach. The Essay help narrates the string matching approach. The source documents are compared to verbatim text overlaps. Suffix trees or suffix vectors are used in this approach. The large documents are not advised to be processed. Bag of words is another method used to locate plagiarized text. This analysis approach represents the adoption of vector space retrieval. The writing is represented as one or multiple vectors.
Citation based plagiarism detection
Another kind of plagiarism identification technique is citation-based plagiarism detection. The analysis is based on citations. Textual content analysis is not considered in this approach. The computer science assignment help narrates the working of this methodology. The similarity in the source reference is searched in other citation sequences. The prototype of the approach exists. But the method is not yet being adopted. The order and proximity are searched for to find similarity between two documents. Some factors are considered to make a successful search. Absolute number or relative fractions are the parameters providing a good search. The pattern degree is analyzed to provide the outcome.
Stylometry
The next plagiarism detection method is known as Stylometry. The statistical approach considers author’s unique writing style to analyze. The similarity between two documents using writing style is examined. The approach is aided to provide authorship attribution. The stylometric models are constructed and compared. This is used for different text segments and passages of the documents.
The detection explained in the writing provides different levels of performance. The Computer science homework solution provides the comparative evaluation for the same. All the methodologies adopt using textual data except citation analysis. Fingerprinting and bag of words depends on the information loss incurred.
Using appropriate chunking and selection methodologies the disguised plagiarized text can be identified. The boundaries of textual similarity can be conquered inn Stylometry method. The approach also aids in identifying disguised and paraphrased plagiarized text.
According to the information science assignment help plagiarism is a crucial element in different kinds of writing. The authors bringing their ideas into writing have to make some considerations. Plagiarism check is one kind of consideration. The essay help suggests that it is a “must-to-do” method. Different kinds of plagiarism detection techniques are explained by the computer science assignment help.
The writing contains the importance of identifying plagiarized check. Fingerprinting, String matching, Bag of words, citation analysis and Stylometry are the different kinds of detection. The working of all the types is detailed in the writing. Each methodology aids the user to detect the plagiarized text to some extent.



 WhatsApp Us
WhatsApp Us